- Log in to the Azure portal at https://portal.azure.com ➢ navigate to the access Azure key vault you created in Exercise 8.1 ➢ select Secrets from the navigation pane ➢ select the + Generate/Import menu item ➢ enter a name (I used csharpguitarBLOB) ➢ and then enter a connection string to an Azure storage account with a blob container (not an ADLS container) resembling the following, into the Secret Value text box:
DefaultEndpointsProtocol=https;AccountName=;AccountKey= ;EndpointSuffix=core .windows.net - Click the Create button ➢ navigate to the Azure Synapse Analytics workspace you created in Exercise 3.1 ➢ open the Manage hub ➢ select Linked Services ➢ select the + New menu item ➢ select an Azure Blob Storage service ➢ click Continue ➢ enter a name (I used csharpguitarBlobWithAKS) ➢ enable Interactive Authoring ➢ select Account Key from the Authentication Type drop‐down ➢ select the Azure Key Value option ➢ select + New from the AKV Linked Service drop‐down ➢ enter a name (I used brainjammerAKV) ➢ select the Subscription from the Azure Subscription drop‐down ➢ select the Azure key vault name you created in Exercise 8.1 and added the secret to in step 1 ➢ select System Assigned Managed Identity from the Authentication Method drop‐down ➢ select the To Secret radio button in the Test Connection section ➢ enter your secret name from step 1 (I used csharpguitarBLOB) ➢ and then select the Test Connection link. Figure 8.43 shows the outcome and configuration. The test connection failed to resolve the failure.
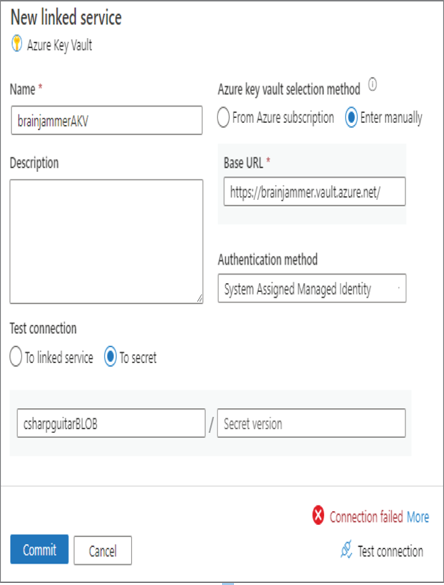
FIGURE 8.43 Access key in Key Vault from a blob linked service failure
- Navigate back to the Azure key vault you created in Exercise 8.1 ➢ select Access Policies ➢ select the + Create menu item ➢ check Get and List from the Secret Permissions section ➢ click Next ➢ search for and add your Azure Synapse Analytics workspace system‐managed identity as the principal ➢ click Next ➢ click Create ➢ test the connection again from the Azure Key Value linked service ➢ and then, when the connection is successful, click Commit.
- On the New Linked Service window, select your secret name from step 1 (for example, csharpguitarBLOB) from the Secret Name drop‐down ➢ select the Test Connection link ➢ and then, when the connection is successful, click Commit. The configuration should resemble Figure 8.44.
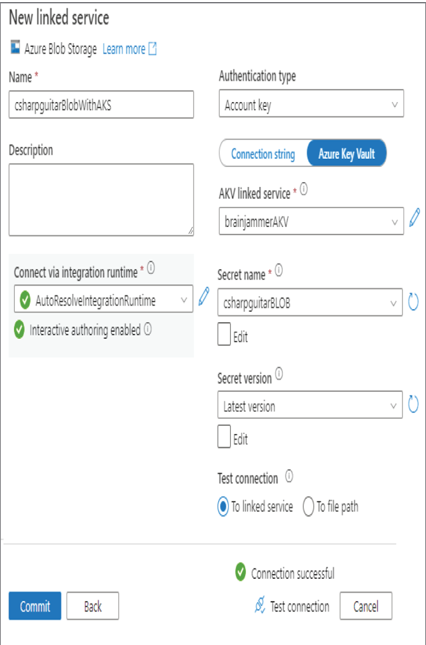
FIGURE 8.44 Access key from Key Vault to blob linked service failure
By default, ADLS access keys configured in Azure Synapse Analytics are stored in a platform‐generated Azure Key Vault secret, which is why Exercise 8.10 used an Azure Storage Blob container instead of ADLS Gen2. In other cases, the access key is encrypted and stored within the context of the workspace. You can see the encrypted access key by viewing the JSON document that describes the configuration of the linked service.
The first action in this Exercise 8.11 was to create a new secret in your Azure Key Vault account and store the connection string as the value. You then proceeded to create an Azure Blob Storage linked service that retrieves the access key from Azure Key Vault instead of storing the credentials locally. This required you to first create a linked service for an Azure key vault, and then target the secret for testing. That testing initially failed because there was no access policy for your Azure Synapse Analytics system‐assigned managed identity on the Azure Key Vault account. Once you provided Get and List to the managed identity, the test worked successfully.
Note that in Figure 8.43 you only provided the secret name, not the version. By default, if no version is provided, then the most current version of the secret is used. You can see this written out specifically in Figure 8.44 in the Secret Version drop‐down list box. When you select Test Connection on the Azure Blob Storage linked service window, the platform pulls the connection string from Azure Key Vault and uses it to test the connection with the storage account. It is recommended in all cases from this point forward to use Azure Key Vault and managed identities when connections to Azure resources are required.



