- Log in to the Azure portal at https://portal.azure.com ➢ navigate to your Azure Active Directory ➢ create a new group named, for example, BRAINJAMMER‐WRITERS (using the same instructions as in Exercise 8.12) ➢ add this group to the Storage Blob Data Reader role as well ➢ navigate to the ADLS container you created in Exercise 3.1 ➢ select the storage browser from the navigation pane ➢ and then navigate to the Confidential folder you created in step 3 of Exercise 8.12, similar to the location shown in Figure 8.49.
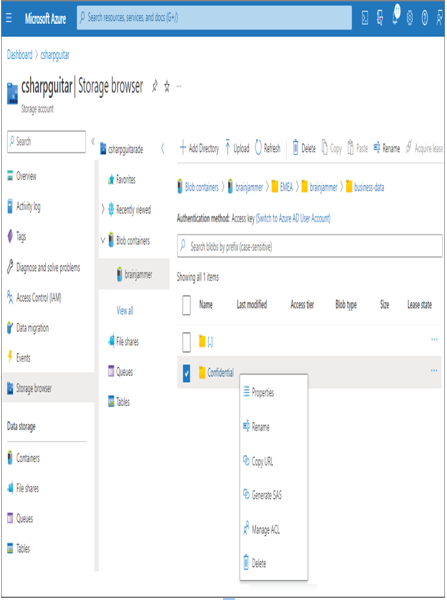
FIGURE 8.49 Managing ACLs for an ADLS folder
- Right‐click the Confidential folder ➢ select Manage ACL from the popup menu ➢ select the + Add Principal option ➢ add the BRAINJAMMER‐WRITERS group ➢ grant Read, Write, and Execute permissions, as shown in Figure 8.50 ➢ and then click Save.
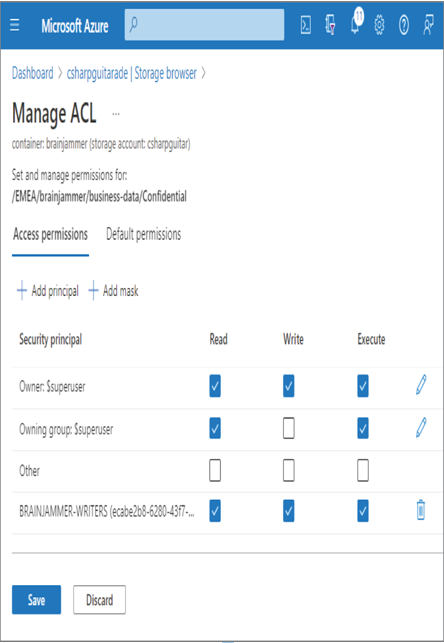
FIGURE 8.50 Adding an ACL to allow write access
- Log in to the Azure portal using the identity of someone in the BRAINJAMMER‐WRITERS group ➢ navigate to the ADLS container created in Exercise 3.1 ➢ navigate one level below the Confidential folder ➢ and then upload and/or modify content within that directory successfully.
- Log in to the Azure portal using the identity of someone in the BRAINJAMMER group ➢ navigate to the ADLS container created in Exercise 3.1 ➢ navigate one level below the Confidential folder ➢ and then upload and/or modify content within that directory unsuccessfully.
Setting up security can be challenging. Delays in the replication of permissions can cause some problems if either the security expert setting up the permissions or the individual needing the permission is impatient. For example, if a permission is granted, an unsuccessful test is performed moments later, and then you make another change, it is possible that the desired permission did not exist long enough to be experienced. Therefore, it is important to be patient, because the permission can take up to 5 to 10 minutes to be applied. The time lag and other challenges experienced setting up security are further justifications for using groups. By using groups, you can grant the permissions and complete the as expected once on that group, and then you add people to the group; you know exactly what permissions they have and that it works. Granting permissions on a case‐by‐case basis would be chaotic and stressful, and it would fail to scale.
Two valuable lessons should come from Exercise 8.12 and Exercise 8.13. The first lesson is that RBAC role assignments are checked before ACLs. That means that if the RBAC role has permissions greater than the ACLs, the permissions of the RBAC are applied. The second lesson is that you cannot use ACLs to reduce the level of permissions that are granted with an RBAC role. That means you cannot take away read access to a file from a group using an ACL if that group is a member of, for example, the Storage Blob Data Reader role. However, you can increase permissions. Both BRAINJAMMER‐WRITERS and BRAINJAMMER are members of the Storage Blob Data Reader role, which gives them read access to all the content on the containers on that account. However, only the BRAINJAMMER‐WRITERS group has write access via an ACL, which then increases the level of permissions on files and directories below the level the ACL permission was applied.
Implement Secure Endpoints (Private and Public)
Network security is the first level of security against improper or malicious access to your data and other resources. Figure 8.1 provides an overview of the network security layer in the context of a layered security strategy. The same applies for networking as it does for security, in that you should engage an expert for professional guidance on how to configure networking and security. Both of those are career worthy, as there exists many complexities that require both skill and experience to create a solution that scales and evolves along with your business. This chapter is intended to get you knowledgeable enough to know some details about security and networking, but not to the degree to design and implement an enterprise‐wide solution. In this section, you will learn about virtual networks (VNets), network security groups (NSG), firewalls, and private and public endpoints.
When you provisioned the ADLS container in Exercise 3.1, you did not bind it to a VNet. Complete Exercise 8.14, where you will create a new Azure storage account and ADLS container that exists in a VNet.